
Instead of an SOS it is better to opt for an SSO.
November
2018
The SSO presents several advantages mainly linked to the possibility of facilitating passwords management: the greater the number of passwords to manage, the greater the possibility that they will be similar, easy to memorize, thus, inevitably lowering the level of security. SSO helps simplify access management to the various services as well as the definition and management of the security policies. Moreover, with this single identification procedure your credentials never leave the authentication domain, you reduce the operational costs as well as the time to access the data. Last but not least, SSO improves the user experience, avoiding users to have to “carry” too many passwords (mentally or in writing!).
The Single Sign On is based on 3 key steps.
Identification - WHO ARE YOU?
Authentication - PROVE WHO YOU ARE
Authorization - ACCESS TO PROTECTED RESOURCES
Which architecture to choose?
The SSO must be integrated and made operational within an architecture that is selected based on specific corporate needs. The are three types of approaches that can be implemented.
Centralized approach.
In this case, you start from a single centralized database of all users with consequent centralization of security policies.
Federated approach.
With a federated approach, different service providers («federated» between each other) manage data belonging to the same user. Access to one of the federated systems allows to automatically access all the other related systems and services. This approach responds to the need for decentralized user management and allows service providers to keep control over their own security policy.
Cooperative approach.
Each user depends on each partner entity to access each service. Each service provider independently manages its own security policy without exchanging user credentials between other entities. This approach responds to the needs of institutional structures in which users depend on a single entity (i.e. Universities, Public Administrations, etc.).
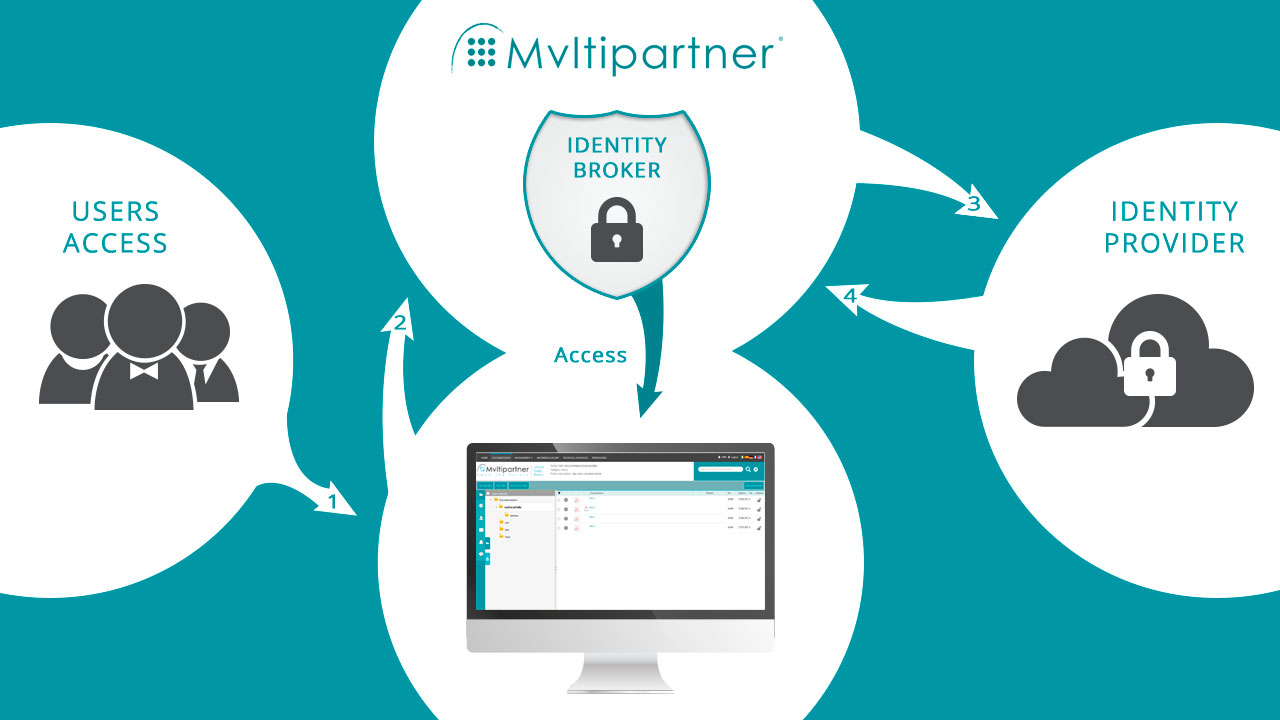
SSO, being the property of an access control system, integrates into an IT architecture designed to receive it (i.e. configured ad hoc) and its task, simplifying the most, is to authorize business users on extra-corporate resources. To do this, it must interface with certain protocols (following are indicated the most common ones):
SAML 2.0 (Security Assertion Markup Language), framework, released by OASIS (Organization for the Advancement of Structured Informations Standard), to exchange authentication, authorization and user information (assertion) between users and federated domains. Currently, it is the most supported and adopted protocol.
OAuth 2.0 is the industry standard protocol for authorization. OAuth 2.0 focuses on the simplicity of client developers while providing specific authorizations flows for Web applications, desktop applications and mobile phones.
OpenID Connect (OIDC) is a simple authentication layer that sits on top of the OAuth 2.0 protocol that allows computing clients to verify the identity of an end-user based on the authentication carried out by an authorization server, as well as to obtain basic profile information on the end-user in an interoperable manner.
SSO and Virtual Data Rooms
Thanks to the versatility of our secure platform, it is possible to integrate access to one or more Multipartner Virtual Data Rooms through SSO automatically and regardless of the type of procedure (centralized, federated or collaborative) adopted by your company. This way, authorized users will access one or more Virtual Data Rooms simultaneously, through a single authentication already verified by your corporate domain. To set up access to our Virtual Data Room through SSO, our technical team needs to interact with your IT department. Find out more on the main features of our Virtual Data Room or request a free demo.





